Socks5 Proxy Configuration and Cross-Border E-Commerce Network Building
I. Synopsis
1. Why do cross-border e-commerce companies need to pay attention to Porfiles configuration?
Cross-border e-commerce plays a key role in the expansion of the global market. However, this field is facing increasingly severe cybersecurity challenges. In order to protect data security and ensure smooth international Internet connections, network engineers are constantly seeking innovative solutions. Among them, Socks5 proxy IP technology is gradually emerging as a powerful tool for improving network security and supporting cross-border e-commerce.
2. What is a SOCKS5 proxy and what are its characteristics?
Residential Proxies have three main protocols, HTTP, SOCKS5 and HTTPS. SOCKS5 is a flexible and powerful network proxy technology. Compared to other types of proxy protocols, SOCKS5 not only supports TCP and UDP protocols, but also provides support for higher-level protocols. This wide range of protocol support makes SOCKS5 Proxies widely used in various network scenarios, including e-commerce platforms, data crawling and streaming media services. Compared with SOCKS4 and HTTP Proxies, SOCKS5 Proxies have improved performance and reliability, significantly reducing error rates and network latency, thereby providing a more stable and efficient network connection.
II. Basic knowledge of SOCKS5 Proxies
1. How does a SOCKS5 Proxy work?
The SOCKS5 proxy protocol acts as an intermediary between the client and the target server, and is responsible for forwarding network traffic. When a user requests access to a website or service, the request packets are first sent to the SOCKS5 proxy server, which then forwards them to the target server. The response packets are also forwarded through the proxy server and then returned to the user. This forwarding mechanism effectively hides the user's real IP address, so that the outside world can only see the IP address of the proxy server, thereby protecting the user's privacy.
In short, the SOCKS5 protocol acts as a middleman, forwarding data between the client and the target host, thereby protecting the user's privacy.
[align=center” target=_blank>[img” target=_blank>https://b352e8a0.cloudflare-imgbed-b69.pages.dev/file/023fb124dde00c3f7c5ee.png” align=”center” />
2. What are Socks5 Residential Proxies for?
First, Socks5 Proxies effectively hide the user's real IP address by acting as an intermediary between the user and the Internet, thereby protecting privacy. Second, Socks5 Proxies not only support TCP and UDP protocols, but can also handle various types of network traffic, including web browsing, file transfers, and real-time applications such as VoIP and online games. In addition, it supports multiple authentication mechanisms to ensure that only authorised users can access services, and can perform domain name resolution to simplify user operations. This is because SOCKS5 Proxies use more modern technologies and algorithms to process data packets, thereby optimising the data transmission process.
It is worth noting that although the SOCKS5 protocol itself does not provide encryption, many service providers have added encryption capabilities to enhance the security of data transmission. In addition, SOCKS5 proxies can effectively bypass geographical restrictions, helping users access geographically restricted content, and improve system performance and reliability through load balancing technology. It also has firewall penetration capabilities, allowing it to connect to restricted networks, while supporting access control and logging, providing administrators with detailed traffic monitoring and security auditing capabilities. In short, with its flexibility and versatility, SOCKS5 proxies have become an important tool for network privacy protection and traffic management.

III.Steps for configuring SOCKS5 proxies
1. How do I choose a reliable SOCKS5 proxy service provider?
Choosing a reliable SOCKS5 proxy service provider is the first step in ensuring the quality of the proxy service. First, you should assess the provider's reputation and user reviews, which can be done by checking online reviews and expert reviews. Second, consider whether the service provider offers detailed technical support and customer service, as these are essential for resolving potential problems.
Thirdly, check their data security and privacy protection policies to ensure that the provider has a clear no-logs policy and encryption measures to prevent user data from being leaked. Finally, assess the coverage and connection speed of their server network and choose a provider that can provide a high-speed, stable connection.
Whether it is an HTTP or SOCKS5 proxy, it is important to choose a trusted service provider. PROXY.CC is a leading provider of IP proxy services, with Residential Proxies that perform well. PROXY.CC offers advanced features and is dedicated to providing the highest standards of data security for both individual and corporate users. Users can choose from over 195 countries worldwide and to date, PROXY.CC has provided efficient proxy services to over 20,000 individual users and more than 100 corporate users. PROXY.CC Proxies support a free trial, which you can experience here.

2. How do I get SOCKS5 Proxy Service information?
Log in to PROXY.CC and purchase the type of proxy you need. Here, we will use Rotating Residential Proxies as an example. Copy the information generated, including the IP address, port, username, and password. [Rotating Residential Proxies User Auth & Pass Extraction Tutorial” target=_blank>
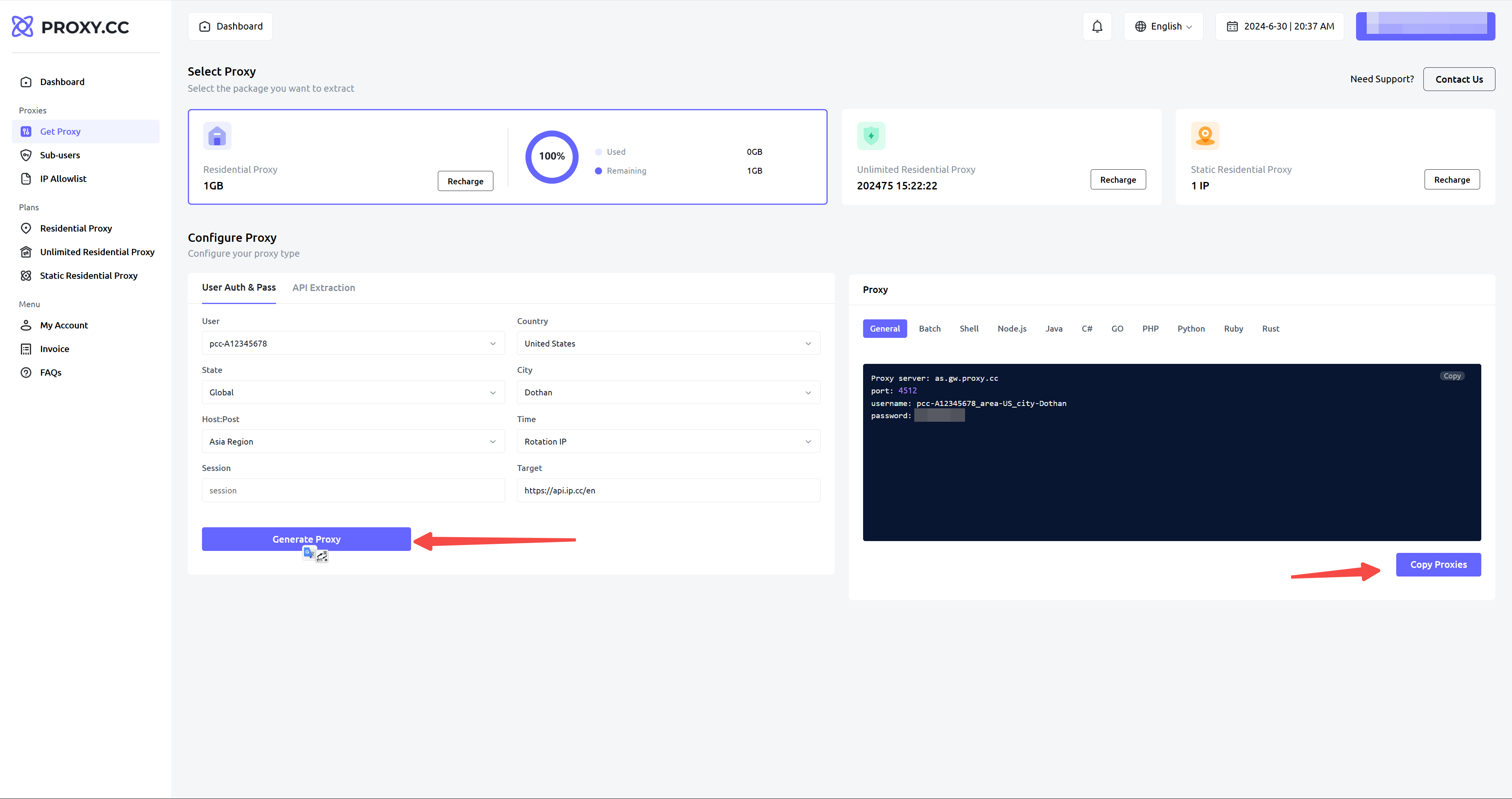
3. How do I use a SOCKS5 proxy in practice?
To configure a SOCKS5 proxy in your browser, open your browser settings, find the network or proxy settings, select manual proxy configuration, enter the IP address and port number of the SOCKS5 proxy server in the SOCKS Host and Port fields, save the settings and restart your browser. For example, in Firefox, open Firefox, click the menu button, select "Options", select "General" in the left menu, scroll down to "Network Settings", click "Settings", select "Manual Proxy Configuration", enter the address and port number of the SOCKS5 Proxy Service in the "SOCKS Host" field, select "SOCKS5", and click "OK".
For more information, please refer to:
Firefox and PROXY.CC Proxy Configuration Tutorial
Google Chrome Proxy Settings Tutorial
After the configuration is complete, open a browser and visit an IP check website (such as whoer.com) to confirm that the displayed IP address is the same as the IP address provided by Proxies.
Visit the target website: visit the target cross-border e-commerce platform to confirm whether the page can be loaded normally. The configuration is now complete.
IV. Frequently Asked Questions and Solutions for Using SOCKS5 Proxies
1. What problems may I encounter when configuring a SOCKS5 proxy?
The following are common problems and their solutions when using a SOCKS5 proxy:
Connection failure: Check the proxy server address, port, network connection and firewall settings.
Authentication failure: Ensure that the username and password are correct and check the proxy server configuration.
Slow speed: Select a server that is geographically closer, check the bandwidth limit and network connection.
Unable to access certain websites:Enable DNS resolution via SOCKS5 or change the Proxy Service.
Applications do not support SOCKS5:Use a supported third-party client software or alternative applications.
Data leakage or privacy issues: Use encrypted transmission and choose a trusted Proxy Service provider.
Frequent disconnections:Ensure a stable network, choose a less loaded server and enable the automatic reconnection function.
2. How can I optimise the performance of a SOCKS5 Proxy?
Optimising the performance of SOCKS5 Proxies can be achieved through a range of technical and configuration measures to ensure maximum data transfer speed and reliability. First, choosing the right Proxy Service is crucial. Choosing a Proxy Service that is geographically close to the target website or service can significantly reduce network latency, while choosing a less loaded server can avoid performance issues caused by overload.
Secondly, a high-performance network connection is the basis for optimisation. Ensuring high-speed broadband and network stability helps to reduce bottlenecks and disconnections. Optimising the configuration of the Proxy Service is also important. Allocating hardware resources such as CPU, memory and bandwidth appropriately and using efficient software can improve processing power and overall performance.
Enabling data compression and caching mechanisms is another effective way to improve speed by significantly reducing the amount of data transferred and the number of times data is transferred. In addition, choosing the right encryption protocol and optimising SSL/TLS settings can improve performance by reducing the overhead of encryption while maintaining security. Load balancing and redundancy are also important. By distributing traffic to multiple servers, you can avoid single points of overload and ensure that the main server can be quickly switched in the event of a failure, thereby improving system reliability.
Regular maintenance and monitoring are essential to keep the Proxy Service running efficiently. Regular updates of the system and software, as well as the use of monitoring tools, can help to detect and solve performance problems in a timely manner, ensuring the stable operation of the Proxy Service.
In terms of client-side configuration, optimising the Proxy settings (such as adjusting the connection timeout and the number of retries) can adapt to different network environments. In addition, enabling the automatic reconnection function can ensure a quick recovery when the connection is lost, thereby ensuring the continuity of the user experience.
V. Summary and recommendations
The importance of SOCKS5 proxies in cross-border e-commerce
In the field of cross-border e-commerce, the use of SOCKS5 proxies is important in the following ways:
Improve access speed and stability:SOCKS5 proxies can help cross-border e-commerce users bypass geographical restrictions and choose the optimal path, thereby improving access speed and stability. Cross-border e-commerce platforms often have geographical restrictions, which can be effectively solved through SOCKS5 proxies.
Ensuring account security: Using a SOCKS5 proxy can hide the user's real IP address, preventing cross-border e-commerce platforms from detecting abnormal behaviour and reducing the risk of account suspension. Proxy Services provide an additional layer of security to protect user privacy and data security.
Supporting multi-account management:In cross-border e-commerce, it is often necessary to manage multiple accounts. SOCKS5 proxies allow users to manage multiple accounts through different IP addresses, avoiding the risk of the platform detecting associated accounts.
Break through network restrictions:In some regions, cross-border e-commerce platforms may be subject to access restrictions. SOCKS5 Proxies can help users break through these restrictions and ensure the smooth operation of their business.
2. How to choose a good Socks5 proxy provider?
When choosing a SOCKS5 proxy service, the following suggestions can help users make a more informed decision:
Service stability: Choose a proxy provider with a good reputation and stable service. The stability of the proxy service directly affects the continuity and stability of cross-border e-commerce business. It is recommended to check user reviews and industry recommendations to determine the stability of the service.
Speed and bandwidth:Ensure that the proxy service provides sufficient speed and bandwidth to meet the needs of cross-border e-commerce business. Higher bandwidth and lower latency can improve page loading speed and response time.
IP address coverage:Choose a proxy service provider with a wide range of IP addresses. Different cross-border e-commerce platforms and markets may have different requirements for IP addresses, and a wide range of proxy services can provide more options.
Security and privacy protection:Ensure that the proxy service provider has good security measures and privacy protection policies. Encrypted connections and strict privacy policies can protect user data security and prevent information leakage.

We recommend using PROXY.CC Residential Proxies, a professional proxy service website that offers three proxy modes: Rotating Residential Proxies, Unlimited Residential Proxies, and Static Residential Proxies. PROXY.CC Proxies supports free trials, click here to experience it.
It aims to provide users with a safe and efficient Internet browsing experience. Whether you are protecting your privacy or need to access content that is restricted in a specific region, PROXY.CC is the ideal choice. We use advanced encryption technology and a strict privacy policy to ensure that all your communications and data transmissions on the Internet are protected in the most reliable and comprehensive way.






